|
Cloud Mining |
||||
|
"Cloud Mining is the process of Bitcoin mining utilizing a remote data center with shared processing power often contracted through a Cloud Mining company. This type of mining allows users to mine Bitcoins without having to manage their own hardware. Since Cloud Mining is provided as a service there is generally some cost, and this can result in lower returns for the miner. |
||||
|
Types of Hosting |
||||
|
Users of hosted Mining equipment can either lease a physical mining server or a Virtual private server and install mining software on the machine. Instead of leasing a dedicated server, some services offer hashing power hosted in data centers for sale denominated in Gigahash/seconds (GH/s); Users either select a desired amount of hashing power and a period for the contract or in some cases can trade their hashing power." |
||||
|
Free Cloud Mining, Is It Possible? |
||||
|
In fact, some of the developers of BitzFree.com are also Bitcoin miners. The main idea is to distribute the developer's bitcoin mining income to the public to spread the Bitcoin Revolution
This is the initial view of Bitzfree |
https://bitzfree.com/?ref=bbUN05YiWRzperCFejYn2B1bbWtFufbWe5u
This is the view of the features that exist in Bitz
My Cloud
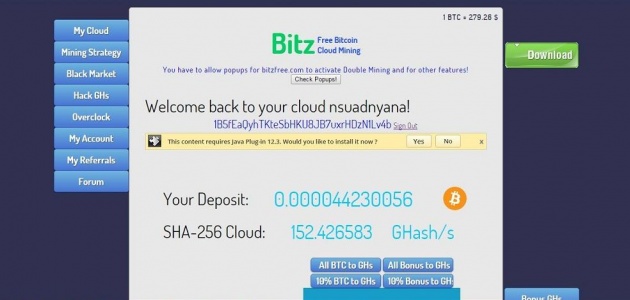
Minning Strategy
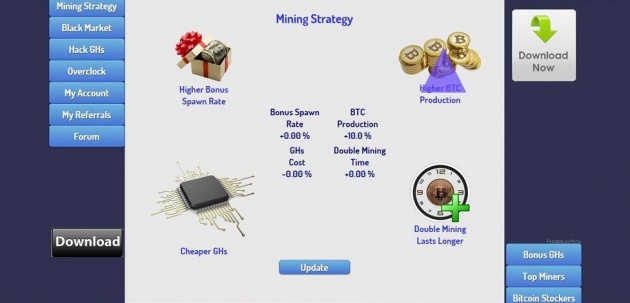
Black Market
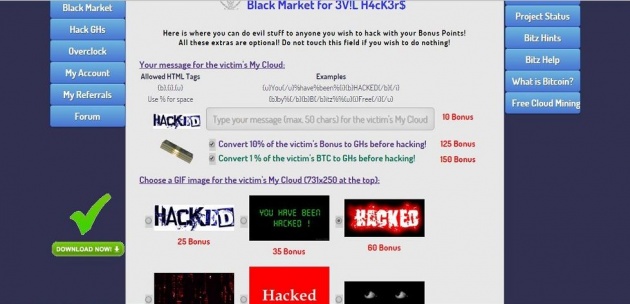
Hacks GHs
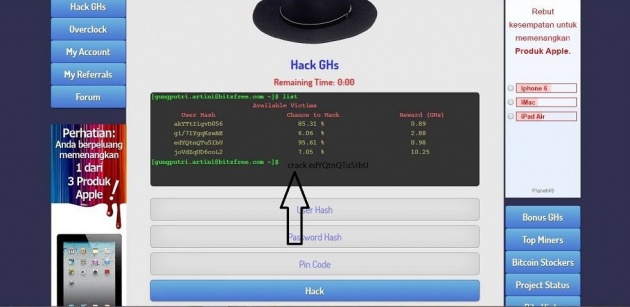
| How to Hack | ||||||||||
| In Hack GHs section: - Type help and you will see two commands: list and crack. list shows the available victims. - Select a user hash from the list which has the highest chance to hack ratio. - Then type crack "userhash". - After cracking is completed, use the given hash combinations on the form under the console. - Then click hack button. Example:
- To crack pakQumozUGRWM's password type crack pakQumozUGRWM. [yourname@bitzfree.com ~]$ crack pakQumozUGRWM User Hash: pakQumozUGRWM Password Hash: 92cea8f9abad186fea7b8481f3c68392 Pin Code: 162 Use these hashes before the victim logins to bitzfree.com - Finally, use the given hash combinations on the form under the console. - Then click hack button.
|
||||||||||
| Rules of Hacking | ||||||||||
| - Beginners have immune to be hacked. You cannot hack a user who has lower than 60 GHs, they are not listed in victims list. - There is a protection system called Probability of Being Hacked for the victims of hacking X = Time passed after you've been hacked in seconds - For each attack, minimum 3% and maximum 16% of the victim's GHs can be hacked. - You can only hack the real GHs. Not the doubled one. For example, if the victim has 500 GHs doubled (in real 250 GHs), you can hack 25 GHs. - Every user has a 100% anti-hacking shield for 2 minutes in each 10 minutes period. These periods are different for each user. - Identities (password hash & user hash) of users are hidden , the attacker cannot find you again and therefore, probability of being hacked again is very low. - You have to wait 2 minutes after a successful hacking operation. - After you have reached 100 GHs level, you have to produce GHs to continue hacking. Actually, Hacking is an advantage for active users. There are many inactive users that have more than 20 GHs. |
Over Clock
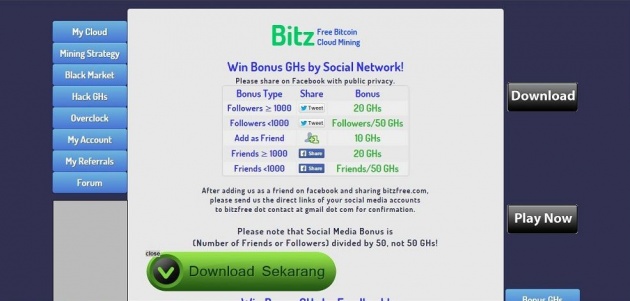
Bonus GHs
| Win Bonus GHs from Social Media Shares |
| Share bitzfree.com and Win Bonus GHs Share from Bonus GHs section and then mail the direct links of your social media accounts to bitzfree dot contact at gmail dot com When sharing on Facebook, please change the privacy option to "public". |
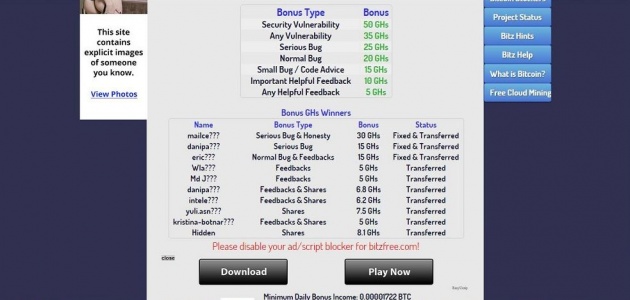
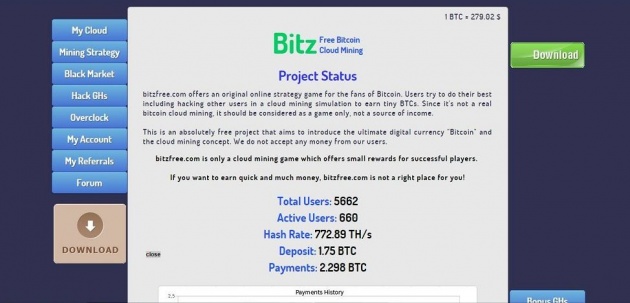
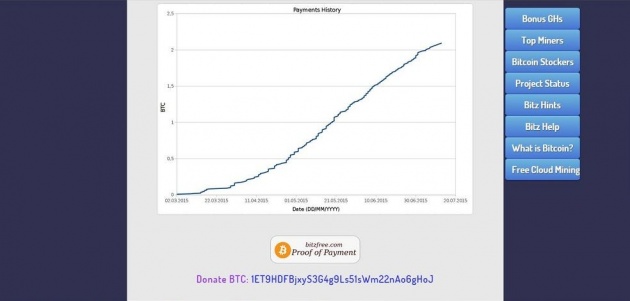
Project Status