US Central Command Social Media Accounts Hacked by ISIS Supporters
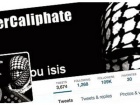
The officialTwitterandYouTubeaccounts for theUS military's Central Command (CENTCOM)that oversees operations in Central Asia and t…

The officialTwitterandYouTubeaccounts for theUS military's Central Command (CENTCOM)that oversees operations in Central Asia and t…

The terrible terrorist attacks in France forced the British Prime MinisterDavid Cameronto consider banning the popular encrypted o…

Security researchers have disclosed local zero dayDLL hijackingvulnerabilities in several applications developed byCorel Softwaret…

Google has once again released the details of a new privilege escalation bug inMicrosoft's Windows 8.1operating system before Micr…

Owning a smartphone runningAndroid4.3 Jelly Beanor an earlier versions of Android operating system ??Then you are at a great risk,…

The stealthy Arduino-based device, dubbed "KeySweeper", looks and functions just like a generic USB mobile charger, but actually s…

Multiple successors of the originalSilk Roadhave come and all have been taken offline in recent years, but aside from selling ille…

n todays world your network is subject to a multitude of vulnerabilities and potential intrusions and it seems like we see or hear…
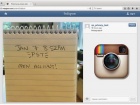
The flaw was first reported byDavid YanofskyatQuartzand Instagram acknowledged the issue last week before patching the flaw. In a …
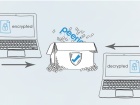
On one end, where governments of countries like Russia is criticizing end-to-end encryption and considering to ban theencrypted co…