The world’s infamous Angler Exploit Kit has become the most advanced, much more powerful and the best exploit kit available in the market, beating the infamous BlackHole exploit kit, with a host of exploits including zero-days and a new technique added to it.
Angler Exploit Kit's newest technique is dubbed "Domain Shadowing" which is considered to be the next evolution of online crime. Domain Shadowing, first appeared in 2011, is the process of using users domain registration logins to create subdomains.
WHAT IS DOMAIN SHADOWING ?
With the help of Domain Shadowing technique used in a recent Angler campaign, attackers are stealing domain registrant credentials to create tens of thousands of sub-domains that are used in hit-and-run style attacks in order to either redirect victims to the attack sites, or serve them malicious payloads.
Security researcher Nick Biasini of Cisco’s Talos intelligence team analysed the campaign and said the "massive" and ongoing Angler campaign targeting Adobe Flash and Microsoft Silverlight vulnerabilities dramatically shooted up in the past three months.
"Domain shadowing using compromised registrant credentials is the most effective, difficult to stop, technique that threat actors have used to date. The accounts are largely random so there is no way to track which domains will be used next," said Nick Biasini.
"Additionally, the subdomains are very high volume, short lived, and random, with no discernible patterns. This makes blocking increasingly difficult. Finally, it has also hindered research. It has become progressively more difficult to get active samples from an exploit kit landing page that is active for less than an hour. This helps increase the attack window for threat actors since researchers have to increase the level of effort to gather and analyze the samples."
HOW HACKERS MADE IT ?
In the recent campaign, the cyber criminals are taking advantage of the fact that most of the domain owners do not regularly monitor their domain registrant accounts, which are typically compromised through phishing attacks. This leverages attackers to create a seemingly endless supply of sub-domains to be used in further attacks.
A new technique called Fast Flux allows hackers to change the IP address associated with a domain to evade detection and blacklisting techniques. Unlike Domain Shadowing which rotates sub-domains associated with a single domain or small group of IP addresses, Fast Flux rapidly rotates a single domain or DNS entry to a large list of IP addresses.
GODADDY ACCOUNTS AT RISK
Cisco has found up to 10,000 malicious sub-domains on accounts — most of them linked to GoDaddy customers, although the security researchers noted that this was not the result of any data breach, but this is because the GoDaddy controls a third of domains on the Internet.
ATTACK VECTOR
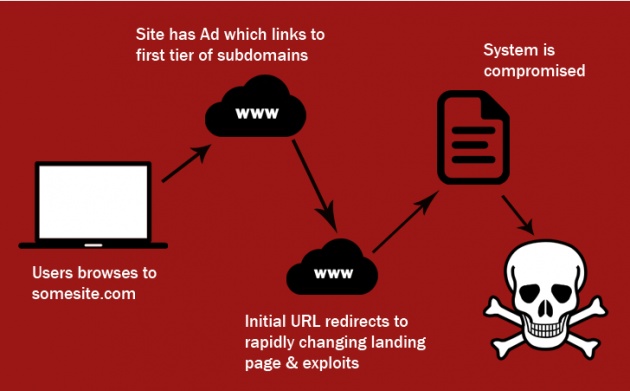
There are multiple tiers to the attack, with different malicious subdomains being created for different stages listed below:
Users are served malicious advertisements on the web browser.
The malicious ad redirects the user to the first tier of subdomains known as "gate".
First tier is responsible for the redirection of victims to a landing page that hosts the Angler Exploit Kit serving an Adobe Flash or Microsoft Silverlight exploit.
This final page is being rotated heavily and sometimes, those pages are active only for a matter of minutes.
"The same IP is utilized across multiple subdomains for a single domain and multiple domains from a single domain account," Biasini wrote. "There are also multiple accounts with subdomains pointed to the same IP. The addresses are being rotated periodically with new addresses being used regularly. Currently more than 75 unique IPs have been seen utilizing malicious subdomains."
With numerous of evasion techniques, zero-day exploits and high level of sophistication, Angler Exploit Kit has elevated as the more formidable hacker toolkits available in the market.
The previous best-selling exploit kit known as BlackHole was known to be the dangerous toolkit, but last year after the arrest of 'Paunch', the mastermind behind infamous BlackHole exploit kit, the exploit kit disappeared from the market.



