Enigma
The story of the cipher machine that changed the world

Hello, guys! I hope everything is going well in your lives. Last night I watched again the movie The Imitation Game, which (you probably know that) tells about Alan Turing and his huge contribution to the end of the World War Second. If Germany had won the War, today we would have lived in a totally different world, probably under a Nazi dictatorship or worse, who knows. So, since I love codes and the machines that implement them, I decided to blog about Enigma, one of the most complex and sophisticated machines in the entire history.
Who created it? How does it work? Why and how was it decoded? These are the questions I will answer in this blog. Are you ready? Let's start!
Video Credits: The Weinstein Company Via YouTube
Introduction: the theory behind the machine
1. The monoalphabetic cipher

Image Credit: NakNakNak Via Pixabay
One of the simplest and most famous encrypting methods is the one used by Julius Caesar; his method is called monoalphabetic cipher, as it uses just one alphabet to encode the message. The first letter of the encoding alphabet differs from the first one of the official alphabet, which starts with the letter A (really? :D). An encryptor, in order to encode his message, has to choose an encoding alphabet that starts with another letter, for instance, F before to start the encoding process. After this procedure, the encryptor writes the clear message, then changes each letter with the corresponding one of the second alphabet and... voilà.

Image Credits: Pixor Via bitlanders
Let's see an example.
Bob wants to send a message to Alice but he doesn't want his wife to discover it; so he has to encrypt it.
First of all, Bob chooses the second alphabet, i.e. the one he will use to encrypt his message; for instance, it starts with F. In this way he associates A to F, B to G, C to H, D to I, E to J and so on. Then Bob writes the message he wants to send to Alice: I LOVE YOU. Lastly, he has to encrypt it by substituting each letter of the clear message with the corresponding one of the encoding alphabet. Let's do it together:
I -> N
L -> Q
O -> T
V -> A
E -> JY -> D
O -> T
U -> ZSo Bob's encrypted message is N QTAJ DTZ.
Bob's wife shouldn't be able to read it. Unfortunately, she found in the trash the paper sheet with the clear message; that's why now Bob is sleeping in the garden under the rain! :D
This kind of encrypting method is very simple but ineffective since Arabs found a very interesting method to decode it without problems. The problem with this code is that it uses the same scheme of the original message: in fact, equal letters in the official alphabet correspond to equal letters in the second alphabet and consequently in the encrypted message, as you can see in the example, in which the letter O was encrypted with a T in either case.
In order to make the code stronger and safer, encryptors invented two new methods: the first one was known as homophonic substitution cipher, in which the more frequently a letter appears in a certain language, the more symbols are used to represent it; the second one is the polyalphabetic cipher, the same used by Enigma.
2. The polyalphabetic cipher
It was used for the first time by the Italian architect Leon Battista Alberti in the XV century; he invented a disc (the cipher disk) made of two wheels, the outer one was fixed and contained all the letters of the alphabet in the right order, the inner one was mobile. This characteristic allowed encryptors to use a new safer method for ciphering their messages.
How did it work? First of all, the encryptor had to choose a key, i.e. a word or, more in general, a group of letters each one of which represented one alphabet; then, he had to write the clear message and, in the end, encrypt each letter of the clear message with the corresponding one of each alphabet.
Let's see another example.
Bob's wife decided to forgive him and allowed him to come back home but this has a price: Bob has to do all the chores, he has to cook, clean the house and bring her wife everything she wants. Bob's life is getting hard, so he decides to send Alice another message; this time he will use another method though.
First of all, Bob chooses a key, for example, LEON. The key has four letters so Bob will use four alphabets to encrypt his new message, that is: HELP ME ALICE. He writes the four alphabets and associates the first word of his clear message to the corresponding one of the first encoding alphabet; the second word of his clear message to the corresponding one of the second encoding alphabet and so on. Let's do it together
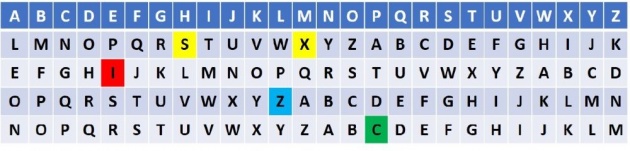
Image Credits: Pixor Via bitlanders
H -> S
E -> I
L -> Z
P -> CM -> X
E -> I
A -> O
L -> Y
I -> T
C -> G
E -> SSo Bob's encrypted message is SIZC XI OYTGS.
This time, Bob destroyed all the paper sheets with the clear message and the alphabets he used to cipher his message, so his wife won't find anything. Unfortunately, Bob left his phone in the living room in which his wife is watching an episode of Sex and the city; she has read the message Alice sent Bob and kicked him out of the house again. Poor Bob :D
This kind of encrypting method is more complex than the first one but it's incredibly safe and the longer is the key the safer it becomes. In fact, as you can notice, a letter can code several different letters. In the example above, the letter S encodes H and E. In this way, it's very difficult to know what letter is associated with each one of the code if you don't know the key. However, this code was violated by Charles Babbage, one of the greatest minds of the XIX century. He showed how it's possible to violate a code whose key has just a few letters.
The Invention of Enigma

Image Credits: fill Via Pixabay
In 1918 Arthur Scherbius founded the Sherbius & Ritter company with his friend; they produced everything from turbines to heated pillows. He has always been searching for new inventions and that's the reason why he decided to invent an electro-mechanic version of the Alberti's ciphering disk: Enigma.
The basic version was made of a keyboard, an exchanger and a display with several bulbs that made the encoded letter lit up. The exchanger unit was made of an intertwining of wires inside a rubber disk: the wire entered from the left side and exited from the opposite one, then entered into the next ones and in the end, through a reflector, the signal reached the last encoded letter, which lit up. After having pressed a letter, the exchanger made a click forward, in this way the same letter was never encrypted in the same way. After 26 keystrokes, the first exchanger completed its rotation and went back to the initial position while the next one made a click forward. With one exchanger or rotor, it's possible to use 26 encoding alphabets, with two rotors 26x26=676, with three ones 26x26x26=17,576 and so on.
The point of strength of Enigma was the huge number of alphabets that it could use and the super fast encoding process, due to the speed of the electric current. Also, there was a reflector that didn't add complexity to the machine but it took the signal coming from the last rotor and sent it back to the display, which lit up and showed the encoded letter corresponding to the digited one; furthermore, if the operator digited the encoded message, thanks to the reflector, he could see the clear message on the display.
The most important information about Enigma was its initial set-up. Even if the enemy had found and taken a machine, it wouldn't have been helpful without the knowledge of the initial set-up. The only thing he could have done was trying day and night to decode the message by testing each one among the 17,576 possible combinations; in this way, after two weeks, more or less, he would have found the key. But if a team of twelve people with twelve Enigma machines had worked at the same time, probably in less than a day they would have decoded the messages. That's why Sherbius added three new elements:
- interchangeable rotors. Since each one had a different path of wires inside it, and since the possible combinations of three interchangeable elements are 6 this multiplied by six the number of possible combinations;
- a multiple socket panel with 12 sockets between the keyboard and the first rotor, which exchanged the electrical paths of two letters before the signal entered in the first rotor.
In this way, the number of possible combinations overcame 10 million of billions. If an operator had checked one combination per minute and worked day and night, he would have spent more than the age of the universe to find the key. That was the power of Enigma.
In the beginning, Sherbius wanted to sell it to businessmen and military but the price he asked (20,000 pounds) didn't convince anyone. However, when Germans knew the reasons why the code they used during the World War First was decrypted, the government bought more than 3,000 machines and at the beginning of the World War Second, Germany had the safest code in the entire history.
The break of the first Enigma

Image Credits: WikimediaImages Via Pixabay
In 1938 Poland, worried about the possible invasion by Russia and Germany, started to work on the decryption of the messages coming from those countries. Their intelligence was the best in the World, since they, for first, recruited also mathematicians besides the linguistic and humanist experts. They got the importance of maths in the cryptography science.
Thanks to a German traitor, they received the instruction manual of Enigma and informations about its inner structure; so, they built a copy of Enigma and studied it. One of the mathematicians who worked at the Polish Bureau, Marian Rejewski, found a relationship between the initial position of the rotors and the six letters of the first message that was sent every day by the German operators. In fact, they used a smart stratagem: they set the machine according to the official instructions and sent twice a new key that was valid just for the message they were about to send. In this way, Rejewski reduced the possible keys to few thousands. In order to found the daily key, he built a machine, called "The bomb", that worked with six Enigma in parallel and thanks to it Polishes could decrypt every German message for a while.
But in 1938 Germans changed Enigma by adding two more exchangers, and four more sockets. These improvements increased the safety of the code and Rejewsky needed 54 more machines in order to continue his work but the cost of those machines didn't allow the Bureau to improve the Polish intelligence system, so he decided to share his discoveries and knowledge with France and Britain, few months before the Poland invasion. In this way, the secrets of Enigma were safe and sound and Allies could have built more copies of the machines and found the way to break the code.
Bletchley Park
Following the polish model, British started to recruit a lot of mathematicians (men and women) at Bletchley Park, not far from London, which became the headquarter of the Government Code and Cypher School (GC&CS). In the big garden in front of the villa, there were a lot of huts; each one was dedicated to a different task: for instance, the hut 6 worked on the decoding of Enigma, the decoded messages were sent to the hut 3, translated in English and confronted with the other pieces of information.
The higher economic resources allowed British to use the polish method to find the initial set-up of Enigma every day; also, the operators used little stratagems to reduce the research time of the daily key: they looked for the "cillies". Cillies were the first six letters of the encrypted message that Germans were used to write for first in their messages. Theoretically, they should have used random words but they used obvious letters like the initial of their names, their love's ones or three close letters on the keyboard. Also, they started to use the same key for all the messages and this allowed British to improve their chances to decode them. Furthermore, British discovered that Germans used two rules:
- don't use the exchangers in the same position of the day before;
- don't connect, throughout a socket, two close letters.
These rules reduced the cryptoanalysts' tables more than a half.
Alan Turing

Image Credits: philcurtis Via Pixabay
In Bletchley Park, the team of cryptoanalysts was made of chess masters, mathematicians, crosswords experts, linguistics, humanists, journalists and so on. However, among them, Alan Turing was the most important one, since his work allowed British and allies to decipher Enigma, although it was continuously modified during the War. Turing worked on a new decrypting method which could have been used if Germans had decided to change their encoding habits, as it happened in 1940.
He solved the problem by noticing that Germans' messages had a rigid structure; for instance, every day after 6 a.m. they were used to transmit meteorological news that contained the word "Wetter" (Weather) almost at the same position. So he thought that, if he knew that at a certain position the encoded sequence corresponded to Wetter, he had just to find the set-up that produced that particular sequence of encoded letters. So he connected several Enigma machines in series so that the signal entered into the first machine and exited from the last one. The input signal was a piece of the encoded word, which he hypothesized being Wetter or any other common word that Germans were used to write every day; the machines tried several positions of the exchangers until one of them had translated one of the letters of the clear word with the one of the encoded message.
In this way, checking all the possible configurations became faster; it required only five hours. There was still the problem of the disposition of the exchangers; in fact, if they had been in the wrong positions, the machine couldn't have found the key and they should have modified them in 60 different ways until the right one. This problem was solved by using 60 machines in parallel, each one set-up in one of the possible combinations. In this way, it was built the first machine able to decrypt Enigma, called Victory, which didn't work as Turing had planned since it was too slow. So British had to wait until 1941 to have the machine that Turing designed: "Agnus Dei" or Agnes, briefly. Fifteen machines were implemented in eight months. With them by their side, if they had been lucky, British could have found the key in only 60 minutes.
The naval Enigma

Image Credits: skeeze Via Pixabay
Each corp of the German army had its own version of Enigma with its own set of keys, so British had different offices to decrypt messages from each corp of the German army.
The hardest one was the naval Enigma, i.e. the one used by the Kriegsmarine. It had a set of 8 exchangers (instead of five) and a mobile reflector so that its number of possible configurations was 6x26=156 times higher than ones of the army version. Furthermore, the naval army didn't repeat twice the key and didn't use stereotyped formulas in their daily bulletins.
In order to get some piece of codes containing known informations, sometimes the RAF bombed a zone in the Atlantic in which there was a U-Boot so that the cryptoanalysts could try to find the key by intercepting the German encoded messages with the geographical coordinates of the attack and use them like cillies. But this strategy wasn't very effective, so they started to bomb the U-boots and steal the keys from them.
The system used firstly by Rejewsky and then by Alan Turing paved the way for the new Era of decryption: the automatic one.
On the final note

Image Credits: FirmBee Via Pixabay
The necessity of the human societies to keep their information secret has always pushed them to encrypt their messages. In the beginning, the encryption methods were simple but the eternal fight between encryptors and decryptors pushed the first ones to invent new, safer and more complex codes, the second ones to improve their methods of decryption. Enigma was the code that changed the history of cryptology; in fact, it drew a line between two Eras: the one in which encrypting and decrypting were made manually and the one in which electronic machines replaced men. Enigma was the most complex code ever invented and Agnes was its worthy opponent; Enigma paved the way for the computer Era, thanks to Alan Turing and his extraordinary mind.
Video Credits: World Science Festival Via YouTube
Thanks for reading, my friends. I wish you the best.
Here, there is a Querlo Chat which you could find useful.
▓▄▀▄▓▀▄▀▓▄▀▄▓▀▄▀▓
Written for Bitlanders
by Pixor
Thanks for your attention.
Pixor, student in electronic engineering at the Polytechnic University of Bari, Italy. Curious and passionate about science, technology, animals, travels, history and music.
Here there are my BLOGS.
¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤
Do you like writing?
Do you want to become a blogger and earn from your blogs?
So, subscribe to bitlanders by clicking HERE and join our big family.
¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤¤
You may also read:
• Holidays in Apulia: what to see, where to go, what to know
• The Majorana particle finally captured. What will happen now?
• Graphene: the material of wonders



