A critical vulnerability has been discovered in the Google Apps for Work that allows hackers to abuse any website’s domain name based email addresses, which could then be used to send phishing emails on company’s behalf in order to target users.
If you wish to have an email address named on your brand that reads like admin@yourdomain.com instead of myemail@gmail.com, then you can register an account with Google Apps for Work.
The Google Apps for Work service allows you to use Gmail, Drive storage, Calendar, online documents, video Hangouts, and other collaborative services with your team or organization.
To get a custom domain name based email service from Google, one just need to sign up like a normal Gmail account. Once created, you can access your domain’s admin console panel on Google app interface, but can not be able to use any service until you get your domain verified from Google.
SENDING PHISHING MAILS FROM HIJACKED ACCOUNTS
Cyber security researchers Patrik fehrenbach and Behrouz sadeghipour found that an attacker can register any unused (not previously registered with Google apps service) domain, example: bankofanycountry.com with Google apps for Work to obtain 'admin@bankofanycountry.com' account.
But obviously, Google would not let you access email service for 'admin@bankofanycountry.com', until domain verification has been completed, which means neither you can send any email from that account, nor you can receive.
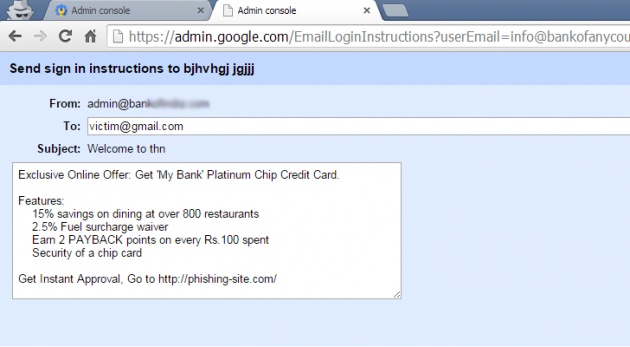
However, the duo explained The Hacker News that there is a page on Google apps that allows domain admin to send 'Sign in Instructions' to the organization users i.e. info@bankofanycountry.com (must be created from panel before proceeding) by accessing following URL directly on the browser.
https://admin.google.com/EmailLoginInstructions?userEmail=info@bankofanycountry.com
Using the compose email interface, as shown, an attacker could send any kind of phishing email containing malicious link to the target users, in an attempt to trick them into revealing their personal information including passwords, financial details or any other sensitive information.
BEFORE SECURITY PATCH
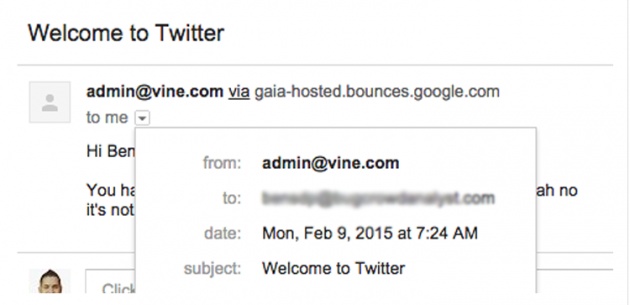
As shown below, researchers successfully obtained admin@vine.com (acquired by Twitter) and send a mail to victim, contains a subject: Welcome to Twitter, which can convince users into submitting their Twitter credentials to the given phishing pages.
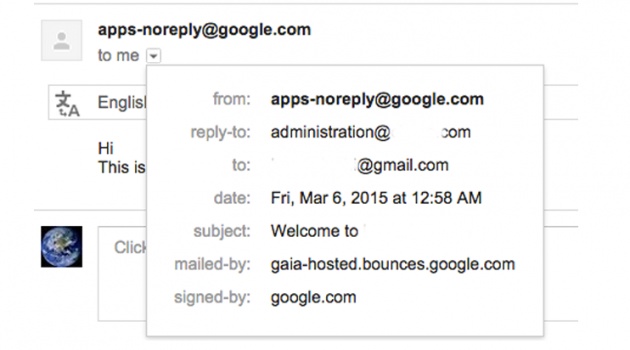
Researchers reported this security and privacy issue to the search engine giant, and the company has applied, what I think, a partial patch to the flaw. As, it is still allowing an attacker to access ‘Send Sign in Instructions’ for unverified domains, but this time via apps-noreply@google.com, instead of the custom email address.
In an email conversation, Behrouz told The Hacker News, "Google believes that showing the sender as apps-noreply is good enough."
AFTER SECURITY PATCH
But, the consequences are still the same because it won’t stop hackers from targeting victims.
Generally, Google automatically helps identify spam and suspicious emails and mark them as spam or phishing warnings, like they're from a legitimate source, such as your bank or Google, but they're not.
However, by abusing above Google vulnerability, hackers could send phishing emails right into your inbox with no warning as the email has been generated from Google’s own servers.



