Hackers have already bypassed Apple's fingerprint scanner using fake fingerprints, and now they have found a way to reproduce your fingerprints by using just a couple of photos of your fingers.
Special Fingerprint sensors have already been used by Apple and Samsung in their smartphones for authentication purposes and in near future fingerprints sensors are believed to be the part of plenty of other locked devices that can be unlocked using fingerprints, just to add an extra layer of authentication. But, How secure are your fingerprints?
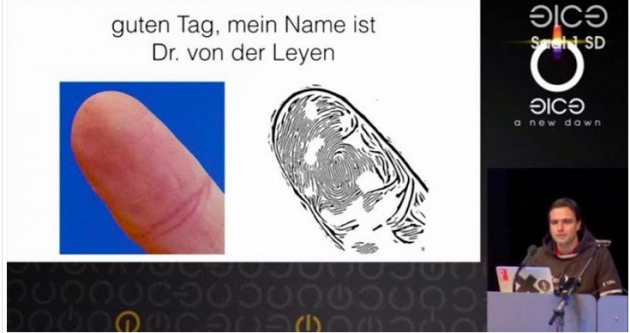
A member of Europe's oldest hacker collective, the Chaos Computer Club (CCC), claimed to have cloned a fingerprint of a Germany's federal minister of defense, Ursula von der Leyen, using pictures taken with a"standard photo camera" at a news conference.
At the 31st annual Chaos Computer Conference in Hamburg Germany this weekend, biometrics researcherStarbug, whose real name is Jan Krissler, explained that he used a close-up photo of Ms von der Leyen's thumbthat was taken with a "standard photo camera" at a presentation in October -- standing nine feet (3 meters) away from the official. He also used several other pictures of her thumb taken at different angles.
Starbug then used a publicly available software program called VeriFinger with photos of the finger taken from different angles to recreate an accurate thumbprint. According to CCC, this software is good enough to fool fingerprint security systems.
"After this talk, politicians will presumably wear gloves when talking in public," Starbug told the audience at the Chaos Computer Conference (CCC) conference.
However, this is not the very first time when Chao Computer Club has targeted fingerprints. In past, the group has demonstrated how easily the Apple iPhone 5s can be unlocked using a fake fingerprint obtained from an individual who has touched a shiny surface, such as glass or a smartphone screen.
"This demonstrates—again—that fingerprint biometrics is unsuitable as [an] access control method and should be avoided," the group said at the time.
Moreover, just three days after the launch of the Galaxy S5, hackers successfully managed to hack Galaxy S5 Fingerprint sensor using a similar method that was used to spoof the Touch ID sensor on the iPhone 5S.
But this recent hack did not require any object 'carrying the fingerprints anymore,' which means that any person could potentially steal someone's fingerprint identity from photos posed on Facebook, Twitter or any social networking site.
This new finding by Starbug potentially calls into question the effectiveness of fingerprint scanners as a security measure. Fingerprints have been supported in the past as biometric identifiers, but because it can be easily reproduced, using fingerprints for security purposes raises questions.
The practical danger is low, because even after obtaining your fingerprint, the data thieves would still need to have your devices or otherwise find a way to sign in using your biometric information. But, the concern is more as the method require no technical skill to perform the fingerprint cloning.



