Less than 24 hours after Google launched the new Phishing alert extension Password Alert, a security researcher was able to bypass the feature using deadly simple exploits.
On Wednesday, the search engine giant launched a new Password Alert Chrome extension to alert its users whenever they accidentally enter their Google password on a carefully crafted phishing website that aimed at hijacking users’ account.
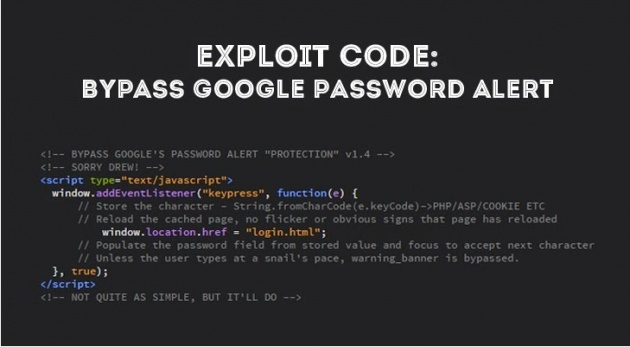
However, security expert Paul Moore easily circumvented the technology using just seven lines of simple JavaScript code that kills phishing alerts as soon as they started to appear, defeating Google’s new Password Alert extension.
Google shortly fixed the issue and released a new update to Password Alert extension that blocked the Moore’s exploit. However, Moore discovered another way to block the new version of Password Alert, as well.
The first proof of concept exploit by Moore relied on a JavaScript that looks for instances of warning screen every five milliseconds and simply removes anything it detects. Generally, the warning screen is still there, but the exploit prevented the user from ever seeing it.
Moore (@Paul_Reviews) posted the proof-of-concept JavaScript exploit yesterday, explaining that Google’s Password Alert can be bypassed by anyone using just seven lines of code.
Here’s the Kicker:
However, Google assured its users that the company has now fixed the issue, releasing Password Alert version 1.4. "To update quickly, go to Chrome://extensions/ , enable developer mode, click update extensions now," Google engineer Drew Hintz said.
But Moore didn’t want to stop here. He began analyzing the code for the extension more closely and figured out another way to bypass Password Alert, effectively killing phishing alerts as soon as they generated.
No simple this time baby:
And according to Moore, the second exploit developed by him will be more difficult for Google to repair.
Moore also provided a proof-of-concept video on YouTube showing the attack in action. You can watch the video below:
Now, let’s see how much time the search engine giant would take to fix this issue in its all new Password Alert Chrome Extension.
The technology was just launched by Google on Wednesday, so you can expect some flaws at its early stage. Password Alert extension has been installed by nearly 30,000 Chrome users, who are advised to update version 1.4, the latest version available at the moment, to fix the first issue.
In order to fix another problem, you may have to wait until Google releases the next update. Till then, you are advised to turn on two-factor authentication and use a good password manager to protect yourself against phishing attacks.
Update: GOOGLE ALERT 1.6 ALSO BYPASSED
After Google released the updated version 1.6 of Password Alert that fixed the second exploit rolled out by Paul Moore, security researchers from Securify firm discovered a way to again bypass Google’s Password Alert feature in the latest version.
The Researchers created a new exploit that works against both Password Alert version 1.5 and version 1.6, which executes in following two steps:
1. Disable Javascript: In HTML, iFrame has a sandbox attribute using which an attacker can disable Javascript for particular iframe only. Following example will completely disable Password Alert. The PoC is fairly simple:

2. Fooling with First 100,000 Blank Bytes: Google Password Alert checks whether a web page looks like a Google Login by looking at the first 100,000 bytes of the HTML. So, this could be bypassed simply by using the following JavaScript:
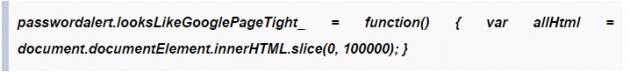
And Boom!



