
The GHOST vulnerability is a buffer overflow condition that can be easily exploited locally and remotely, which makes it extremely dangerous. This vulnerability is named after the GetHOSTbyname function involved in the exploit.
Attackers utilize buffer overflow vulnerabilities like this one by sending specific packets of data to a vulnerable system. The attack allows the attacker to execute arbitrary code and take control of the victim’s vulnerable machine.
Unfortunately, the vulnerability exists in the GNU C Library (glibc), a code library originally released in 2000, meaning it has been widely distributed. Many derivative programs utilize the glibc to carry out common tasks. Although an update released by Linux in 2013 mitigated this vulnerability, most systems and products have not installed the patch.
What Can I Do About GHOST Vulnerability?
Like with any vulnerability, the best way to mitigate GHOST vulnerability is to identify vulnerable systems, prioritize the remediation process based on asset criticality, and deploy patches. You should keep a current inventory of devices, operating systems, and applications in your network so that you can answer the question ‘am I vulnerable?” before some bad actor answers it for you.
AlienVault Unified Security Management (USM) can also help. USM provides asset discovery, vulnerability assessment, threat detection (IDS), behavioral monitoring and SIEM in a single console, plus weekly threat intelligence updates developed by the AlienVault Labs security research team.
USM can scan your network to identify assets with the GHOST vulnerability, making it easy for you to identify systems that need to be patched and prioritize remediation
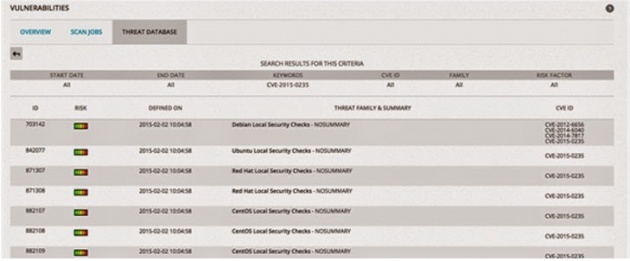
Not only can USM identify vulnerable systems, it can also help you detect attempted exploits of the vulnerability. Within hours of the discovery of the GHOST vulnerability, the AlienVault Labs team pushed updated correlation directives to the USM platform, enabling users to detect attackers attempting to exploit it.
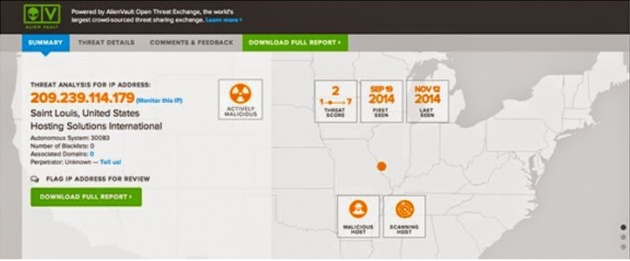
USM also checks the IP information against the Open Threat Exchange (OTX), the largest crowd-sourced threat intelligence exchange. In the example below, you can see details from OTX on the reputation of an IP, including any malicious activities associated with it.
Learn more about AlienVault USM:
Download a free 30-day trial
Watch a demo on-demand
Play with USM in our product sandbox (no download required)



