There's a new and clever way of hacking into computers, and it can be done cheaply – Using just a radio receiver and a piece of pita bread.
Yeah, you heard it right. Security researchers at Tel Aviv University have demonstrated how to extract secret decryption keys from computers by capturing radio emissions of laptop computers.
Capturing the radio signals to steal data from a computer system is nothing new. But the process required expensive, bulky lab equipment to accomplish.
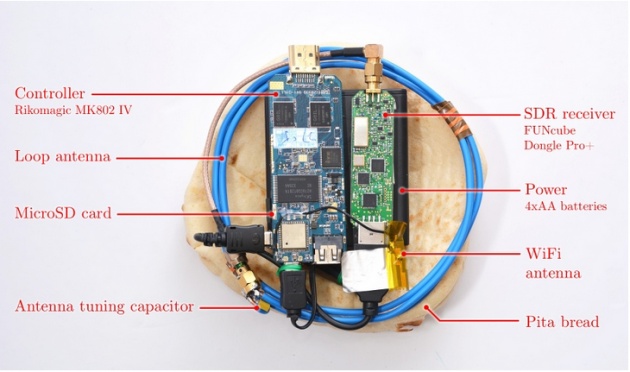
However, the Israeli-based researchers team managed to do it with cheap consumer-grade components as well as small enough to hide inside a piece of pita bread.
Using cheap equipment, the team of researchers, including Daniel Genkin, Lev Pachmanov, Itamar Pipman and Eran Tromer, was able to capture keystrokes, applications running on a computer system, and encryption keys.
How the method works?
The idea is simple, as different computer operations, such as playing some game or decrypting and encrypting a file, have their own characteristic pattern of radio activity signals, depending upon CPU power usage.
An attacker can send an encrypted passages of text in an email to a target computer and then monitor the radio signals when the computer starts decrypting the specific email, making it possible for an attacker to extract the key used to secure data.
According to researchers, to assemble the device, hacker would only need:
FUNcube Dongle Pro+ software-defined radio
Android-based Rikomagic MK802 IV mini-computer to control the dongle
AM radio antenna
A piece of pita bread to hide all the above components
But why is the pita bread necessary?
It's because the radio device is small enough to be concealed inside a pita bread, a sandwich, or any other thing that would not going to attract any attentions in public spaces.

Once demonstrating the attack in Lab, the team created a mobile version, dubbed the Portable Instrument for Trace Acquisition (Pita), which the researchers managed to hide inside a piece of pocket bread.
Now, this method could be used by the hackers to spy on public targets, even without their knowledge, though the attacker should be at the distance of about 50cm (1ft 8in) from the targeted laptop, said the researchers in a paper detailing their work.
Using this technique, the researchers say they were able to crunch the data and get the password in a matter of few seconds.
You can go here for the full detailed explanation of how the device is built and how it operates. However, the team has planned to present their finding at a technical conference on cryptographic hardware in September.



