The computer giant Lenovo has released a tool to remove the dangerous "SuperFish" adware program that the company had pre-installed onto many of its consumer-grade Lenovo laptops sold before January 2015.
The Superfish removal tool comes few days after the story broke about the nasty Superfish malware that has capability to sneakily intercept and decrypt HTTPS connections, tamper with pages in an attempt to inject advertisements.
WE JUST FOUND 'SUPERFISH' - LENOVO
The Chinese PC maker attempted to push the perception that Superfish software was not a security concern and avoid the bad news with the claim that it had "stopped Superfish software at beginning in January".
However, Lenovo has now admitted that it was caught preloading a piece of adware that installed its own self-signing Man-in-the-Middle (MitM) proxy service that hijacked HTTPS connections.
"We did not know about this potential security vulnerability until yesterday," Lenovo said in a statement released on Saturday. "We recognize that this was our miss, and we will do better in the future. Now we are focused on fixing it."
'SUPERFISH' WENT BAD TO WORSE
The Superfish malware went bad to worse when Errata Security's Robert David Graham cracked and published the password that would allow anyone to unlock the certificate authority and bypass the computer's web encryption. The password with the right software could allow a hacker to insert malware or potentially spy on a vulnerable Lenovo user sharing the same Wi-Fi network.
United States Computer Emergency Readiness Team (US-CERT) also warned Friday that Superfish malware could be exploited to "allow a remote attacker to read all encrypted web browser traffic (HTTPS), successfully impersonate (spoof) any website, or perform other attacks on the affected system."
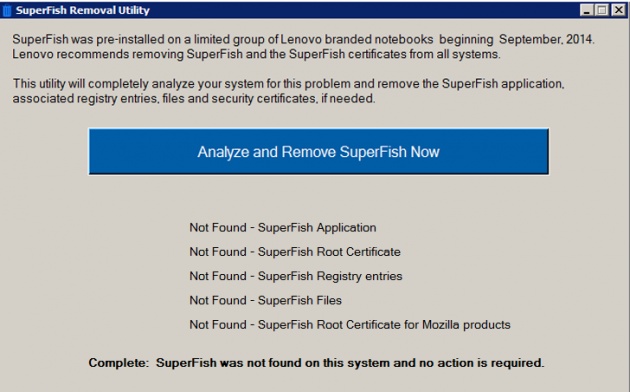
AUTOMATICALLY REMOVE 'SUPERFISH' COMPLETELY
Lenovo joined hands with Microsoft and McAfee, and created a custom uninstall tool to clean your computer of the Superfish malware program and its CA certificates, and in a responsibly transparent move, also posted the source code and license of the removal tool for scrutiny.
"We apologize for causing these concerns among our users - we are learning from this experience and will use it to improve what we do and how we do it in the future," the company said.
The company has released an "automated tool", which the PC maker says will "ensure complete removal of Superfish and Certificates for all major browsers."
If in case users don’t prefer to use the automated tool, the company has also provided a step-by-step process for how to remove SuperFish manually.
CHECK FOR 'SUPERFISH' MALWARE NOW
SuperFish is an adware that tampers with your computer’s encryption certificates, which seemingly leaves your otherwise "encrypted" communications insecure whenever you are on a shared WiFi connection (like at a coffee shop). It can silently intercept and decrypt HTTPS connections, tamper with pages and inject advertisements.
Superfish is present on Lenovo laptops sold between September 2014 and January 2015, although the company says no Thinkpads were shipped with the Superfish malware. Still, you can check your Lenovo computers for this nasty software with the help of a test created by researcher Filippo Valsorda.



