
After HeartBleed, POODLE and FREAK encryption flaws, a new encryption attack has been emerged over the Internet that allows attackers to read and modify the sensitive data passing through encrypted connections, potentially affecting hundreds of thousands of HTTPS-protected sites, mail servers, and other widely used Internet services.
A team of security researchers has discovered a new attack, dubbed Logjam, that allows a man-in-the-middle (MitM) to downgrade encrypted connections between a user and a Web or email server to use extremely weaker 512-bit keys which can be easily decrypted.
Johns Hopkins crypto researcher Matthew Green along with security experts from the University of Michigan and the French research institute Inria has discovered LogJam a few months ago and published a technical report that details the flaw.
Logjam — Cousin of FREAK
Logjam encryption flaw sounds just like FREAK vulnerability disclosed at the beginning of March.
The FREAK encryption-downgrade attack allows attackers to force SSL/TLS clients, including OpenSSL, to weaken ciphers over the web so that they can easily decrypt the intercepted HTTPS connections.
Freak is an implementation flaw, but Logjam is due to a flaw in the basic design of the transport layer security (TLS) protocol itself, making all web browsers and some mail servers that use TLS to establish secure connections with end-users vulnerable.
Logjam can be exploited on a subset of servers that support the widely used cryptographic algorithm called the "Diffie-Hellman key exchange," which allows protocols like HTTPS, SSH, SMTPS, IPsec to negotiate a secret key and create a secure connection.
Reasons to worry about Logjam vulnerability:
The flaw allows an attacker to trick a web browser into believing that it is using a regular key, not the export key version.
Many PCs reuse the same large numbers to generate the keys, which makes them easier for attackers to crack.
The flaw has been present for more than 20 years affecting HTTPS, SSH, IPsec, SMTPS, and other protocols that rely on TLS.
The flaw affects any server supporting DHE_EXPORT ciphers and all modern browsers. An estimated 8.4 percent of the top one Million sites and a significant percentage of mail servers are vulnerable to the new vulnerability because they support those export keys.
90s WEAK EXPORT-GRADE ENCRYPTION
Like Freak, Logjam is another exploit that takes advantage of legacy encryption standards imposed by the U.S. government in the 1990s-era on US developers who wanted their software products to be used abroad.
The regime was standardized by the Clinton administration so that the Federal Bureau of Investigation (FBI) and other US intelligence agencies like NSA (National Security Agency) could easily break the encryption used by foreign entities.
"To comply with 1990s-era U.S. export restrictions on cryptography, SSL 3.0 and TLS 1.0 supported reduced-strength DHE_EXPORT cipher suites that were restricted to primes no longer than 512 bits," reads the paper.
Let's revisit Snowden Leaks:
A large bunch of NSA confidential documents leaked by former NSA employee Edward Snowden revealed the Global mass surveillance programs, including the mass crypto attacks carried out by the agency but the documents didn't mention how they actually made it possible.
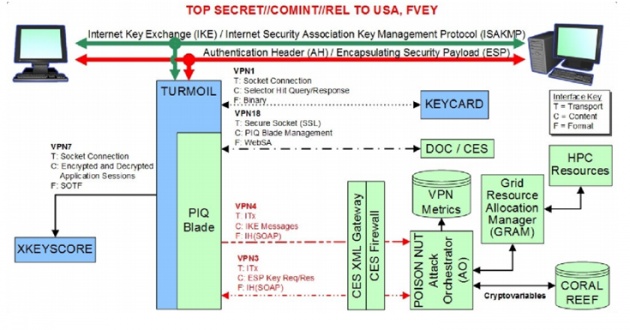
I think disclosure of Logjam attack made it somewhat clear that how the NSA with large amounts of computing power would have been able to break even the stronger encryption that uses the widely used algorithm.
"A close reading of published NSA leaks shows that the agency's attacks on VPNs are consistent with having achieved such a break," the paper notes.
Check Now! If Yor are Vulnerable to Logjam
You can check whether your browser is vulnerable by clicking here. At the time of writing, some major browsers are still vulnerable to the Logjam attack. However, Google security team is already working to increase the SSL requirement in Chrome to 1024 bit.
How to Protect Yourself?
Security researchers recommended all server administrators to disable support for the export-grade (DHE_EXPORT) cipher suites that allow Diffie-Hellman connections to be downgraded, and generate a new and unique 2048-bit Diffie-Hellman group.
The researchers who discovered the flaw have also provided a detailed guide with step-by-step instructions for securely deploying Diffie-Hellman for TLS, as well as more technical details of the vulnerability on their website.
Moreover, users are strongly encouraged to install browser and e-mail client upgrades as soon as they arrive. Also, developers should use the latest libraries and reject Diffie-Hellman groups shorter than 1024 bits.



