 Many of us own a PayPal account for easy online transactions, but most of us don’t have balance in our PayPal Account. But what will happen if your money doubles, triple...or even more folds in just some couple of hours ?? Sounds cherishing!! A loophole in the popular digital payment and money transfer service, PayPal allows its users to double the money in their account and that too endlessly. That means with only $50 in your PayPal account, you can make it to $100, then $100 to directly $200 and so on. An eBay owned company, PayPal provides a faster and safer way to pay and get paid. The service gives people simpler ways to send money without sharing financial information, with over 148 million active accounts in 26 currencies and across 193 markets, thereby processing more than 9 million payments daily.
Many of us own a PayPal account for easy online transactions, but most of us don’t have balance in our PayPal Account. But what will happen if your money doubles, triple...or even more folds in just some couple of hours ?? Sounds cherishing!! A loophole in the popular digital payment and money transfer service, PayPal allows its users to double the money in their account and that too endlessly. That means with only $50 in your PayPal account, you can make it to $100, then $100 to directly $200 and so on. An eBay owned company, PayPal provides a faster and safer way to pay and get paid. The service gives people simpler ways to send money without sharing financial information, with over 148 million active accounts in 26 currencies and across 193 markets, thereby processing more than 9 million payments daily. According to TinKode a.k.a Razvan Cernaianu, who claimed to have found this loophole in the PayPal service that actually resides in its Chargeback Process which could be exploited to do fraud with PayPal.
Tinkode is a convicted former Romanian hacker, who was arrested in year 2012 for attacking NASA, Oracle, Pentagon, U.S. Army and many more high profile websites and that time he was ordered to pay damages totalling more than US$120,000.
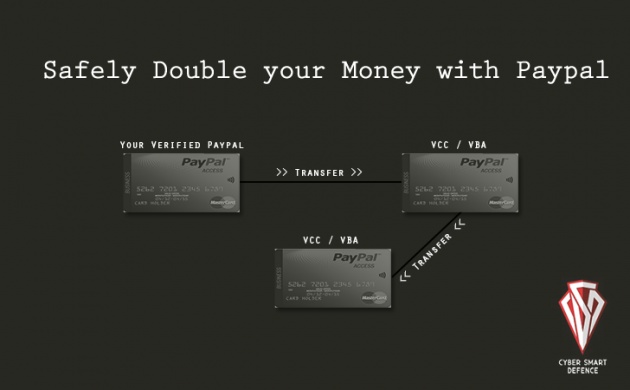
“A Chargeback, also known as a reversal, occurs when a buyer asks a credit card company to reverse a transaction that has already cleared” and this could be done when the buyer's credit card number is stolen and used fraudulently or if seller tries to fraud. He noticed the flaw while making a transaction using PayPal with a person back in 2010, who was trying to scam him with his money using the same chargeback process. To avoid paying charges, he transfer all his money from his temporary account to his another, real PayPal account. But, when he checked after a month, he noticed that his account balance was negative i.e. $50. Exactly this trick he demonstrated to PayPal security team, which allows anyone to double their amount endlessly. In a proof of concept explanation he detailed that by making three separate PayPal account with one real and other two verified using Virtual Credit Card (VCC) and Virtual Bank Account (VBA). POC Scenario:
TinKode already reported the flaw to PayPal Security team for bug bounty and they admitted it as a flaw in their Terms of Service (ToS), but not as a web application vulnerability. “While the abuse described here is possible in our system, repeated abusive behavior by the same and/or linked account(s) is addressed.” PayPal replied. TinKode is not eligible for bug bounty, but we thank him for exposing this fraud technique that could be already in use by some criminals to generate money illegally. Anyone with little technical knowledge can reproduce this trick, but readers are advised to do not try to use this trick as PayPal could ban your account permanently.
Tinkode is a convicted former Romanian hacker, who was arrested in year 2012 for attacking NASA, Oracle, Pentagon, U.S. Army and many more high profile websites and that time he was ordered to pay damages totalling more than US$120,000.
“A Chargeback, also known as a reversal, occurs when a buyer asks a credit card company to reverse a transaction that has already cleared” and this could be done when the buyer's credit card number is stolen and used fraudulently or if seller tries to fraud. He noticed the flaw while making a transaction using PayPal with a person back in 2010, who was trying to scam him with his money using the same chargeback process. To avoid paying charges, he transfer all his money from his temporary account to his another, real PayPal account. But, when he checked after a month, he noticed that his account balance was negative i.e. $50. Exactly this trick he demonstrated to PayPal security team, which allows anyone to double their amount endlessly. In a proof of concept explanation he detailed that by making three separate PayPal account with one real and other two verified using Virtual Credit Card (VCC) and Virtual Bank Account (VBA). POC Scenario:
“So for example, you have 500$ on your account. You transfer the money to the second account with the pretext of buying a phone. From the second account you again transfer the money to the third account as a gift. After 24 hours, use the charge-back function from the first account (the real one) to get the money back, with the excuse that the phone did not arrive on time. PayPal will initiate a process where both sides bring evidence for their defense. Obviously you will only send evidence from the first account showing that you were scammed. At the end of the trial the money will be restored to the primary account and the second account will have a negative balance of -500$. This way, you doubled the initial amount of money because you still have 500$ in the third account. As the second account is only a virtual one, it will not have real money from which PayPal can extract. Therefore you are left with 500$ restored by PayPal, and 500$ in your third account.”
TinKode already reported the flaw to PayPal Security team for bug bounty and they admitted it as a flaw in their Terms of Service (ToS), but not as a web application vulnerability. “While the abuse described here is possible in our system, repeated abusive behavior by the same and/or linked account(s) is addressed.” PayPal replied. TinKode is not eligible for bug bounty, but we thank him for exposing this fraud technique that could be already in use by some criminals to generate money illegally. Anyone with little technical knowledge can reproduce this trick, but readers are advised to do not try to use this trick as PayPal could ban your account permanently.