A new and terribly awful breed of Point-of-Sale (POS) malware has been spotted in the wild by the security researchers at Cisco's Talos Security Intelligence & Research Group that the team says is more sophisticated and nasty than previously seen Point of Sale malware.
The Point-of-Sale malware, dubbed "PoSeidon", is designed in a way that it has the capabilities of both the infamous Zeus banking Trojan and BlackPOS malware which robbed Millions from US giant retailers, Target in 2013 and Home Depot in 2014.
PoSeidon malware scrapes memory from Point of Sale terminals to search for card number sequences of principal card issuers like Visa, MasterCard, AMEX and Discover, and goes on using the Luhn algorithm to verify that credit or debit card numbers are valid.
The malware then siphon the captured credit card data off to Russian (.ru) domains for harvesting and likely resale, the researchers say.
"PoSeidon is another in the growing number of malware targeting POS systems that demonstrate the sophisticated techniques and approaches of malware authors," researchers of Cisco’s Security Solutions team wrote in a blog post.
"Attackers will continue to target POS systems and employ various obfuscation techniques in an attempt to avoid detection. As long as POS attacks continue to provide returns, attackers will continue to invest in innovation and development of new malware families."
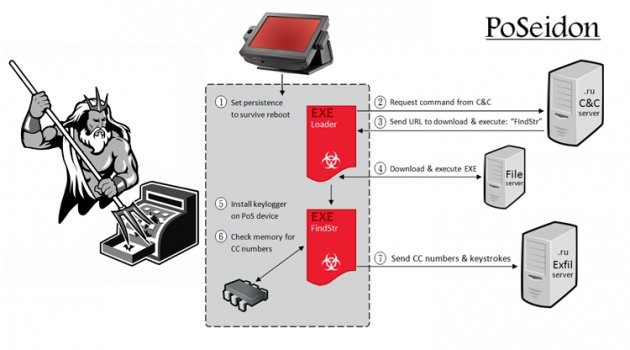
The components of PoSeidon are illustrated in the diagram above.
Poseidon Point of Sale malware comprises of a Loader binary that maintains persistence on the target machine in an attempt to survive reboots and user logouts. The Loader then receives other components from the command and control servers.
A subsequently downloaded binary FindStr installs a Keylogger component which scans the memory of the PoS device for credit card number sequences.
The identified numbers are verified using the Luhn algorithm and then encrypted and sent to one of the given exfiltration servers, majority of which belongs to Russian domains:
linturefa.com
xablopefgr.com
tabidzuwek.com
lacdileftre.ru
tabidzuwek.com
xablopefgr.com
lacdileftre.ru
weksrubaz.ru
linturefa.ru
mifastubiv.ru
xablopefgr.ru
tabidzuwek.ru
In past few years, a number of Point of Sale malware has been spotted in the United States, collecting users' credit card magnetic stripe data, and selling them in underground black markets.
Network administrators should remain vigilant and must adhere to industry best practices so that they can protect themselves against advancing Point of Sale malware threats, the researchers say.



