
A critical remote code execution vulnerability has been reported in the eBay owned global e-commerce business PayPal that could be exploited by an attacker to execute arbitrary code on the PayPal's Marketing online-service web-application server.
The remote code execution flaw, discovered by an independent security researcher, Milan A Solanki, has been rated Critical by Vulnerability Lab with a CVSS count of 9.3 and affected the marketing online service web-application of PayPal.
LIKE US ON FACEBOOK:
The vulnerability resides in the Java Debug Wire Protocol (JDWP) protocol of the PayPal's marketing online service web-server.
Successful exploitation of the PayPal vulnerability could result in an unauthorized execution of system specific codes against the targeted system in order to completely compromise the company's web server, without any privilege or user interaction.
JDWP is a protocol that used for communication between a debugger and the Java virtual machine that it debugs. It is one layer of the Java Platform Debugger Architecture (JPDA).
However, JDWP does not use any authentication, but could be abused by hackers to execute arbitrary code remotely onto the affected Web server.
Solanki also provided a proof-of-concept video to demonstrate the hack in action. He used the jdwp-shellifier tool from Github to scan the marketing sites and found opened port 8000.
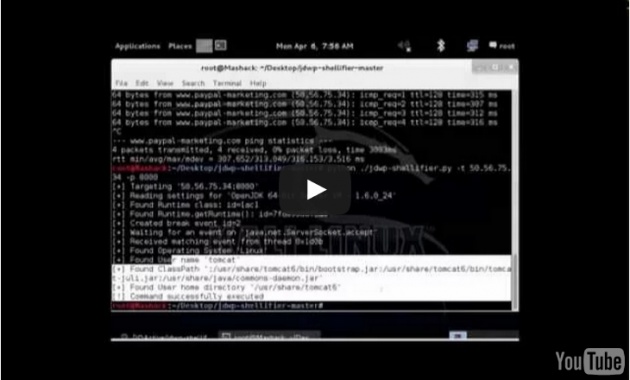
The opened port 8000 made him establish a connection to the service without any authentication that allowed him to execute his server-side codes with root privileges. This is nothing but a successful exploitation of the remote code execution flaw.
Solanki reported the vulnerability to the Paypal developer team, and without any long delay, the team fixed the flaw within four days after receiving the details from security researcher.



