
GoPro, the popular wearable high-definition camera manufacturer, has vulnerability in its official website that exposes usernames and passwords of thousand of its customers’ wireless network.
Action camera maker GoPro manufactures cameras which are compact, lightweight, rugged, and are wearable or mountable on vehicles. GoPro cameras capture still photos or video in HD through a wide-angle lens.
GoPro offers a mobile app to its users that gives you full remote control of all camera functions — take a photo, start/stop recording and adjust settings.
You need to connect to the wireless network operated by your camera, and the GoPro app gives you instant access to the GoPro Channel to view photos and play back videos, then share your favorites via email, text, Facebook, Twitter and more.
FLAW EXPOSES WIRELESS PASSWORD
Security researcher Ilya Chernyakov reported The Hacker News team that GoPro camera update mechanism could expose your wireless username and password to the hackers.
Recently, Chernyakov borrowed a GoPro camera from his friend, who forgot its GoPro password. So, he decided to recover the password of the camera by updating the camera firmware manually, as mentioned on the GoPro website.
In order to get camera update files, one needs to follow instruction available on the GoPro website. "It is pretty simple procedure, with Next -> Next -> Finish that ends up with a link, to a zip file. When you download this file, you get a zip archive which you supposed to copy to a SD card, put it in your GoPro and reboot the camera," he explained.
Archive Download Link generated by GoPro website for Chernyakov’s device:
http://cbcdn2.gp-static.com/uploads/firmware-bundles/firmware_bundle/8605145/UPDATE.zip
When he opened the archive rar file, he found a file named "settings.in", which contained the desired settings for the camera, including his wireless network’s name and password in plain text, as shown in the figure.
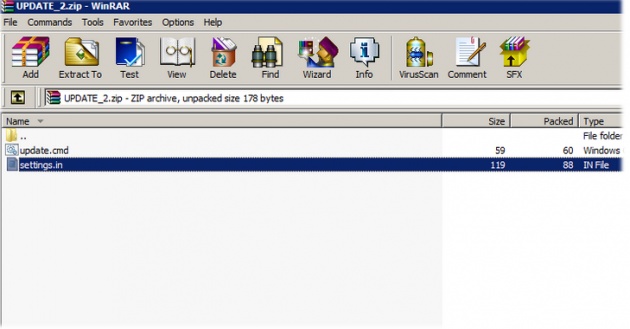
You need to notice the numeric characters (red bold) contained in the above archive URL, representing some sort of serial number referring particularly to Chernyakov’s camera.
COLLECTING THOUSANDS OF WIRELESS PASSWORDS
Chernyakov noticed that GoPro website is not using any kind of authentication for providing archive download for each customer and changing the numeric value +/- to any digit in the above URL can expose customized archive for other customers.
He wrote a python script to automatically download the file for all possible numbers in the same serial and collected more than thousands of wireless usernames and passwords, belonging to the GoPro customers, including his own.
Obviously, wireless password are of no use unless the attacker is not in the range of any targeted wireless network, but exposed username/password list could be used by attackers in a simple password dictionary brute-force attacks in various attacks.
Chernyakov reported the vulnerability to the company, but haven’t heard back from them. The affected list of customers could be wide as GoPro is the popular camera maker and the company recently reported fourth-quarter revenue of $634 Million, which was more than doubled the company’s third-quarter sales.



