Social Engineering: When People Are the Weakest Link

Image credits: Computer Security by TheDigitalWay via Pixabay.com & Canva.com Being a network engineer, and having to help people……







Image credits: Computer Security by TheDigitalWay via Pixabay.com & Canva.com Being a network engineer, and having to help people……

The term Hacking is always considered to be a negative thing but in reality it can be used to help peoples espacially those who are……
For a long time , I've been seeing people fighting over whether which language is better , which language to learn , and what I get……
Programmers have always been fond of watching movies related to topics like coding, AI, Hacking etc. But if we think the way round……
For a long time , I've been listening around , why 'CODING' ?Why learn "Programming" , what's that cool in it ?Even I've listened……

Hello bitlanders world, Once again it is Deep Shelter with another interesting and informative blog post about Hacking but……

Photo Credit: Lost Angeles Times via http://www.latimes.com Hello everyone, I’m back for the second part of my……

(image source: itsecuritything.com)Yahoo logo. Hello everyone! It’s nice to be back blogging. I’ve been stuck doing drawings……

The role of QUERLO in the INFORMATION DRIVE involving INTERNET PRIVACY, YAHOO! BREACHES and few of the most WANTED HACKERS in the……

Photo Credit: Google Photo via http://fortune.com Yahoo Data Breaches and what QUERLO could do to help resolve……

The words Internet Privacy seem like an oxymoron. It feels like it is impossible to protect your privacy, everything about you is……

Photo Credit: Image created via BeFunky.com Hello, guys! As a good friend of mine recently informed me, Micky has given……

Usage of electronic mail has been a hit from the time it was introduced until this very day. Email as it is addressed as an acronym……

Internet privacy/Data privacy. Image Credit: money.cnn.com Yahoo! data breaches "The Internet service company Yahoo! reported……

Whatsapp 4G VIP SCAM - Technical Analysis Rafay Baloch 19 hrs ago This is a short blog post describing about a recent hoax pertaining……

b Today i am gonna tell you about About Hacking because most of you don't know about "What is hacking?" & "How they Hack?".……

LETS HACK WHATS-APP ACCOUNT Need to Hack WhatsApp Account? The following is a WhatsApp Hack Guide with full Instructions! Figure out……

How Download Kali Linux 2.0 Urdu-Hindi How Download Kali Linux 2.0 Urdu-Hindi
A handheld tool that holds a set of probes. Each probe wirelessly connects back to the device for commands and for reporting data.……
Steps to card Ebay succcessfully :- Things You Needed :-1.eBay Account ( Good Account with Feedback Score 30-90 ) Reason : This will……

Do viruses, DDoS attacks, or buffer overflows tickle your fancy? If so, you might consider becoming a legal hacker, aka an ethical……
Hey guys, I just wanted to share some info about Clickjacking. It's basically low to medium risked issue but the sometimes the risk……
Are u ready to hacking ? Cek Now Hacking Ebook 2016

If you've ever worked in the Command Prompt for very long, you know that it can be really frustrating executing the cd/chdir command……

What's a Hacker? Brian Harveycollege of California, Berkeleyin a single sense it is stupid to argue approximately the ``true'' that……
Hi Friends. Now a days CCTV cameras are used many place like shops, malls, offices, warehouse etc and more. for security reason and……

Basic Security Testing with Kali Linux Book Details Paperback: 310 pages Publisher: CreateSpace Independent Publishing……

This book is targeted at information security professionals, penetration testers and network/system administrators who want to get……
Here is how you do a cool little hack with notepad. What it does is pops up a command prompts and overloads the computer and the computer……

Hi, My name is Abbas and I am Admin at HaCoder . Here you will find latest news related to hacking around the world, current affairs……
Hi guys. Im sure you all use facebook and want max amount of likes on your facebook pics and posts. Here is the solution. Go to...……
Hi friends, sometimes you might get surprised when you see blank status or blank comment or any other such things on facebook wall……
Hacking is an Engaging Field but is surely not easy.To Become a Hacker one has to have an attitude and Curiosity of learning……

Russian researcher known as the “Dark Purple” in the online world. He, along with his colleagues from his workplace, created……

Russian researcher known as the “Dark Purple” in the online world. He, along with his colleagues from his workplace, created……

Russian researcher known as the “Dark Purple” in the online world. He, along with his colleagues from his workplace, created……
How to Hack A Facebook AccountAnd How To Protect yourself From HackersPlease take note that this is for educational purposes only……

I just did the latest Tatiana Show about Hacking culture and history as well as how Bitcoin plays into it.
Not sure how critical this one is. Does not affect all servers and you still need serious power to crack keys http://www.wired.com/2015/05/new-critical-encryption-bug-affects-thousands-sites/……
http://haktuts.blogspot.in/search/label/NEWS
A RAT is also a shortcut called Remote Administrator Tool. It is mostly used for malicious purposes, such as controlling Android……
Google adalah search engine yang terbesar dan sampai saat ini blum tertandingi, yang hampir menandinginya adalah bing search……
yeeehh, this my first blog post, and of course i was confuse about what i will write, so i decide to introduce my self.. i love cyber……
yeeehh, this my first blog post, and of course i was confuse about what i will write, so i decide to introduce my self.. i love cyber……

freehacksandcheats.com all version available here of games and hacking software .you play any game easily and download hacking software.and……
NOTE:Its just for educational purpose.Don't use this skill in wrong way. 5 Ways to hack a Facebook account, something most of our……

Some important advantages of internet are as follows: 1. Information search: ……
Realy Unbelivable, You Must Read This Friends...! A 4 Year Kid Hacked FBI's Database. 11 August, 2014Los Angeles| A 4-year old kid……

i am admin of annontricks.com and i present a special tricks for you guys. Windows 7 is a great improvement after the release of windows……
How to Identify and Avoid Phishing Scams Phishing is a form of social engineering technique used by hackers to gather sensitive information……
This time i am going to talk about the hacking by Indian Hackers. KARACHI: Official website of Pakistan People’s Party (PPP)……
Likes.com, one of the emerging social networking site and popular image browsing platform, is found vulnerable to several critical……

Till now we have seen a series of different malware targeting Windows operating system and not Mac, thanks to Apple in way it safeguard……

Many of us own a PayPal account for easy online transactions, but most of us don’t have balance in our PayPal Account.……

The Internet is a big place filled with lots of “Free” offers for this and “Essential” programs for that,……
Every one know that hacking is crime but i think it's not if u ethical Here basically 3 types of hackers - i)White Hat ……
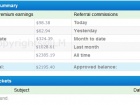
Ito ay isang napaka-simpleng maikli at madaling gabay na makakatulong sa iyong makakuha ng sa paligid ng $ 15 sa bawat pag-download……

Source: IamSatoshi Brett Scott, author of The Heretic’s Guide to Global Finance: Hacking the Future of Money (sold for Bitcoin),……

Source: IamSatoshi Circuit bending art, code and activism, raising awareness to Bitcoin giving a Carte Blanche in the Forex market,……

Source: IamSatoshi Book For You? Post-Crisis Adventures in Financial Subversion. The Heretic’s Guide to Global Finance: Hacking……
Follow the Below steps to convert direct download files into Torrent Files. Steps :- 1) Go to www.Burnbit.com/ 2) Now to Right Click……

When internet got famous and almost every person who was curious, started to use internet, mainly because they would like to communicate……

As in the Previous blog i told u about phishing requires mind skills. You need to convince the victim to log in to the fake page .……

Phishing is the most modern way and the Simplest way to hack a Facebook account . In phishing fake pages are used also called as "spoofed……

This is the most important issue now a day but most of us really unaware of it. As we all know the use of the Bluetooth feature in……

All records have a security aspect. Most people are sensitive about how much they earn and do not want all their colleagues to share……

Digital literacy helps you communicate and keep pace with modern global developments. In the social media and network integration……

In previous post I introduced a simple extension to remove Ads from browser in this post I will show you how to remove Massages icon,……

Competition with the goal of uncovering sustainable approaches to information and communication technology (ICT) kicked off February……